
“Cyber security” & “Data privacy”
Services

Governance > Risk > Compliance Management & Assessment
ISO 27001, NIST

Data Privacy & Assessment
GDPR

Penetration
Testing
By subject matter experts
Secure Network Design & Assessment
ISO/IEC 27033

Disaster
Recovery
By subject matter experts
Cyber Security Framework (NIST)
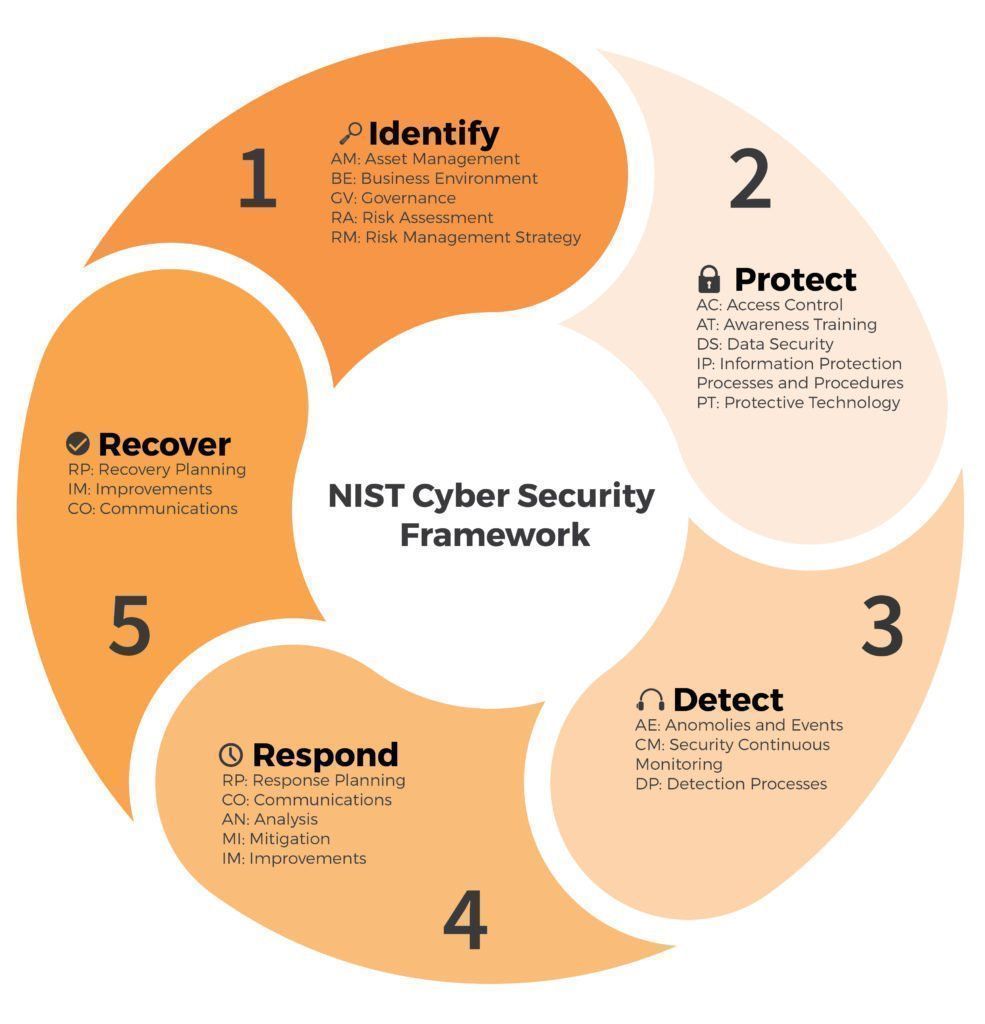
1. IDENTIFY
Know Thyself!
Risk assessment is the first step to protect your company.
Is it easy?
No! There is a high probability that you do not have any documentation in place.
Are you ready to be transparent and start documenting?
No!
Then, Do Not Call Us!
Cybersecurity risk assessments help organizations understand, control, and mitigate all forms of cyber risk. It is a critical component of risk management strategy and data protection efforts.
2. PROTECT
Awareness and Training (PR.AT)
Protective Technology (PR.PT)
Information Protection Processes and Procedures (PR.IP)
Data Security (PR.DS):
3. DETECT
Do you really know what is happening in your environment?
AE : Anomalies and Events
CM : Security Continuous Monitoring
DP : Detection Processes
4. RESPOND
When the things go really wrong nobody knows what to do. Are you one of them? If not, what have you prepared?
RP: Response Planning
CO: Communication
AN: Analysis
MI: Mitigation
IM: Improvements
5. RECOVERY
There is always a probability that you will lose data, either of a cyber attack or as a result of technical issue.
As the recent breach of 50 million T-Mobile users’ data made clear, today’s organizations are more vulnerable than ever to data breaches. During the pandemic, cyber attacks with financial windfalls have hit companies hard across sectors. With its fifth data breach in the past four years, T-Mobile is an example of a company that has fallen victim to multiple cyber-attacks — and they are certainly not alone. Do you have a proper full functioning backup plan and process?
Do you have disaster recovery plan?
Do you have an action plan?
Let’s work together on your security
If you would like to improve your cyber security resilience